This is an article by industry expert Heidi Horn that also appears in TechNation.
When it comes to implementing an effective medical device cybersecurity program, it’s easy for healthcare technology management (HTM) teams to quickly get overwhelmed.
So, where should you begin?
While the eventual goal should be a fully mature operational technology (OT) security program, the reality is that budget and staffing constraints often prevent HTM teams from achieving this all at once. That’s why the crawl, walk, run approach—one where you establish pieces of your program over time—may be the most effective method.
Let’s examine what that might look like.
Step 1 – Crawl: Establish One Inventory for All Your OT Assets
When it comes to implementing an effective OT security program, you can start by improving what you already have—your medical device inventory.
In a recent article published in MedTech Dive, Allan Friedman with the Cybersecurity and Infrastructure Agency stated, “You can’t defend what you don’t know about.”
With that in mind, make sure you have an updated and consolidated inventory—preferably in a mature computerized maintenance management system (CMMS)—that includes all medical devices, including those often-overlooked ones in the lab, medical offices, and ambulatory care centers.
When it comes to OT security, your CMMS should not only have the capabilities to capture maintenance history and contract or warranty information, but it should also be able to capture pertinent security information like whether the device is networked, its IP and MAC address, its ePHI capabilities, and what operating system it’s running.
Since the inventory and its associated data is constantly changing, you also need to shore up your processes for identifying all new devices, capturing the needed information during asset onboarding, and verifying data accuracy through ongoing audits and planned maintenance cycles. A modern CMMS —like Nuvolo Connected Workplace—can automate the onboarding process to ensure all pertinent data is collected.
Likewise, an often forgotten (but critical) step in ensuring an accurate inventory is disposing of equipment while documenting in your CMMS that required procedures were followed. A mature CMMS can automate much of this disposition process for you.
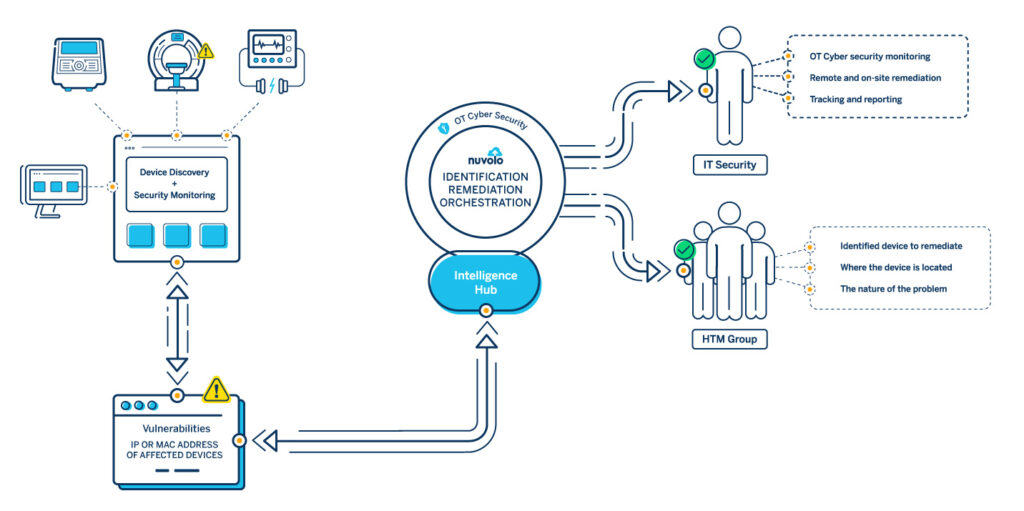
Step 2 – Walk: Integrate Your CMMS’ Inventory with an OT Discovery and Security Monitoring Tool
Utilizing a solution like Nuvolo OT Security allows you to integrate your CMMS with an OT device discovery and security monitoring tool like Armis, Asimily, CyberMDX, Cynerio, MedSec, Medigate, Order, or Paloalto (to name a few).
By integrating your Nuvolo CMMS with one of these tools, you can identify and automatically add to your CMMS any new medical devices placed on the hospital network. In addition, when a cyber threat is identified through the security monitoring application, you will be alerted through your CMMS with the information you need to respond, including the asset number, the device type/manufacturer/model, where it is located, who supports the device, and whether it’s currently in use.
Step 3 – Run: Orchestration and Remediation Workflows
The final step to implementing a mature medical device cybersecurity program is getting all of your data (often coming from multiple sources) into one place to produce actionable workflows.
Nuvolo’s OT Security solution gives HTM departments the tools and resources to make this process painless by:
- Assessing each device’s cybersecurity risk
- Applying applicable settings to ensure an effective cybersecurity posture
- Tracking updates to the security settings
- Enabling workflows that help orchestrate responses to threats
Also included in the Nuvolo OT Security solution is access to Mayo Clinic Healthcare Technology Management Cybersecurity and Operations library of security settings that can be used during device evaluation and onboarding. Mayo Clinic based its security framework on National Institute of Standards and Technology (NIST) and the Association for the Advancement of Medical Instrumentation (AAMI) standards.
To learn more about how Nuvolo can help you develop an effective medical device cybersecurity program, explore our OT Security and Connected Workplace for Healthcare solutions.
About the Author
Heidi Horn, MA, AAMIF is Vice President of Product Marketing-Healthcare for Nuvolo. She has over 20 years of experience as a leader in the healthcare technology management (HTM) industry. Horn was the 2019 recipient of AAMI’s “HTM Leadership Award” and is well-known for her transformational work leading SSM Health’s 120-person HTM department for more than a decade. Horn is also heavily involved with AAMI and serves as a member of AAMI’s Board of Directors as well as chair of AAMI’s Technology Management Council and its HTM Standardization sub-team. She is also an inaugural member of the AAMI Fellow program.