Stories about data breaches are becoming increasingly common.
Some of these breaches cause lasting reputational damage for the victims, and in extreme cases, it costs them immediate financial damage in the form of ransom money or stolen funds.
So why does this keep happening?
The short answer is that data—and control over data systems—can be incredibly lucrative. And as long as this remains true, hackers will find ways to exploit digital systems to collect data or otherwise manipulate the inner workings of an organization.
A Looming Issue in Healthcare
For the healthcare industry in particular, this is a major issue.
According to the American Hospital Association (AHA), the U.S. is home to 6,210 hospitals, each with 50 to 500 beds and 10 to 15 networked devices per bed. That translates to approximately 14 million connected medical devices at the bedside—which represents a lot of incentive and opportunity for hackers.
And the risk extends far beyond just bedside devices. In fact, a 2020 IoT Threat Report from Palo Alto Networks’ Unit 42 threat security team found that 83% of Internet-connected medical imaging devices (like MRI and X-ray machines) are susceptible to hacking.
And even if hackers have no interest in manipulating those specific machines, it’s possible for them to hack the machines to gain access to other parts of the hospital’s digital infrastructure—like patient databases.
This is known as lateral movement.
Once hackers find an entry point within a network, they can infiltrate multiple other devices and systems—oftentimes before IT departments or device managers have any clue what’s happening. And when you consider that in a 500-bed hospital there are over 7,500 network-connected devices and systems, it’s easy to see that there are lots of potential entry points.
What’s more, this type of incident is often more financially devastating for healthcare organizations than those in other industries.
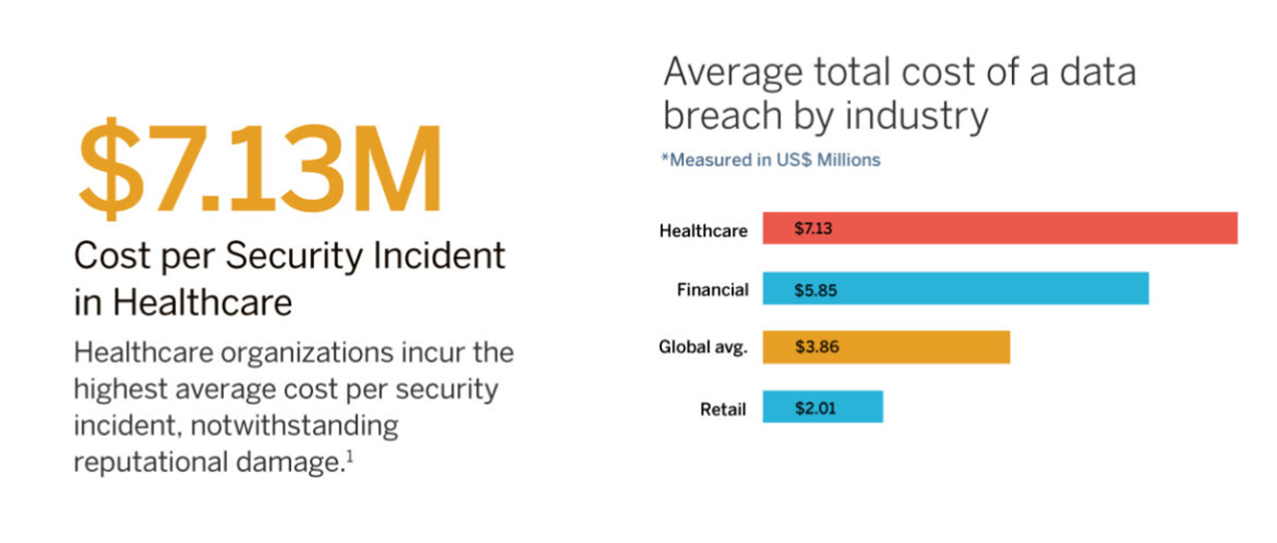
Source: Ponemon Institute & IBM Security, “2020 Cost of Data Breach Report”, 2020
Why Are So Many of These Devices Left Vulnerable?
Any operational technology (OT) device connected to the Internet can be hacked. And ironically, these devices are particularly vulnerable to attacks because they tend to be overlooked as vulnerabilities.
This happens for a number of reasons, including:
- Lack of a complete inventory: Many healthcare organizations still track assets and equipment using spreadsheets or other disparate systems. This tends to create ambiguity, uncertainty, and inaccuracies when it comes to maintaining their medical devices.
- Obsolete operating systems: Each device has its own operating system, and unless someone is manually tracking and installing updates, there’s a good chance that the OS will become outdated before anyone notices. And when the provider is no longer releasing updates to protect the OS, the device instantly becomes vulnerable to new security threats.
- No standard onboarding process: Whenever a new device is added to an organization, it’s important to know when and where it was added, as well as what its security settings should be. Many hospitals don’t track this, and their new, connected devices are easily lost, forgotten about, and/or not configured for optimum security.
- Disjointed cybersecurity management procedures: One of the biggest challenges for hospitals is knowing the cybersecurity status of all their devices and equipment. If they don’t keep this information in one system, it’s difficult to know which devices are being properly maintained and which ones are being left wide open to external attacks.
How Hospitals Can Close the Security Gap
Device security is crucial for hospitals to maintain their patient care, financial health, and reputational status.
We’ve explored the downsides of lackluster security and why it happens in the first place. But the good news is that there is a proven set of steps hospitals can take to ensure their devices are protected at a high level at all times.
These include:
- Creating a single inventory of every device in the organization, both connected and non-connected
- Using industry standards to establish security procedures for device onboarding, such as implementing strong default passwords, confirming installation of the latest software patches, and checking for vendor-recommended network and security settings
- Integrating the inventory with security and monitoring tools, so that when a security event occurs, responders can see the full context of each affected device—including what it is, where it is, who supports it, what OS and patch it has, whether it’s currently in use, etc.
- Implementing a service management platform that automatically dispatches engineers or technicians to quickly address security issues
The steps listed above can drastically reduce the probability and impact of an OT-related security breach. In fact, companies with automated responses see the average security lifecycle decrease in duration by nearly one quarter.
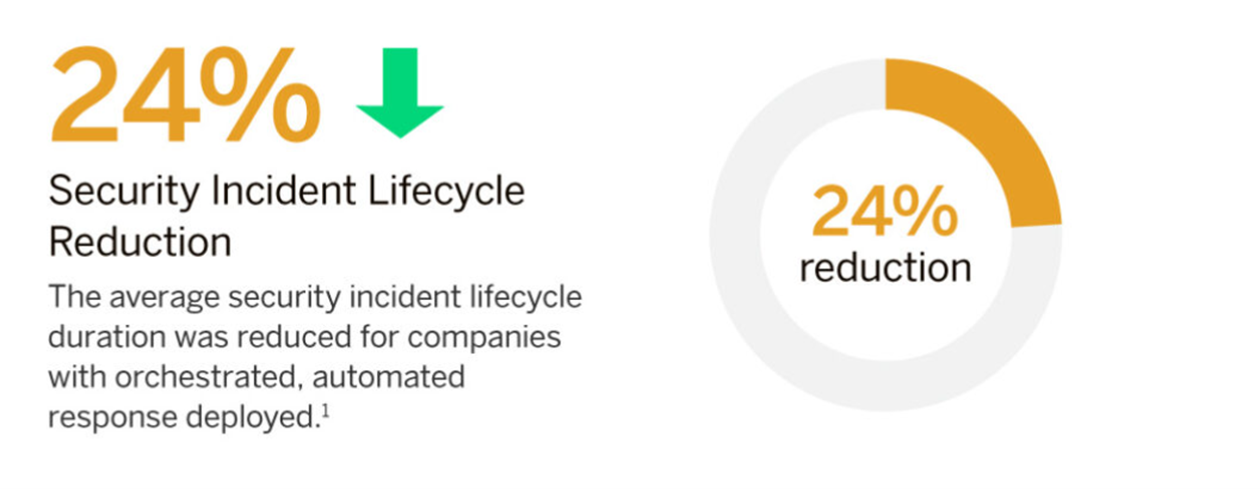
Source: Ponemon Institute & IBM Security, “2020 Cost of Data Breach Report”, 2020
A fully connected integrated workplace management system (IWMS) like Nuvolo Connected Workplace makes all of this possible.
It establishes a single, trusted inventory for enterprise-wide use, integrates with third-party security and monitoring tools, and auto-generates work orders when security issues are detected. Plus, it offers the ability to create workflows for onboarding processes, so every device is set up like it should be.
Visit this link to learn more about Nuvolo’s OT Security solution and how it helps hospitals keep a watchful eye on all of their medical devices and systems.