OT Security
Protect Your Critical Operations
Ensure the safety, accessibility, and availability of all your operational technology (OT).
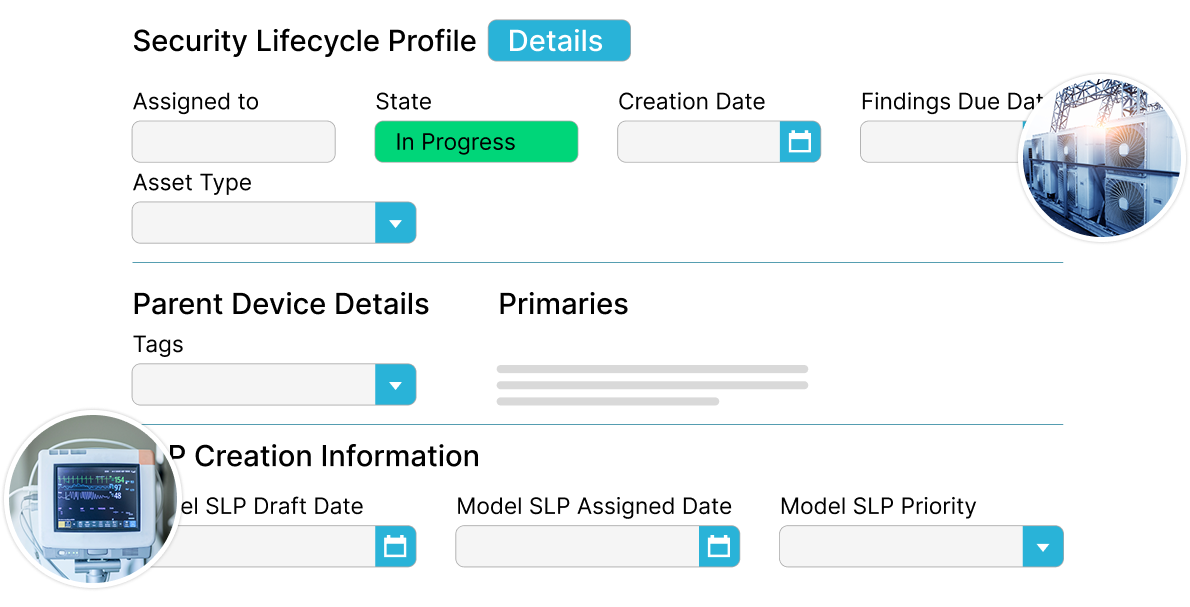
Know the Status of All Your OT Assets
Have visibility into all of your operational technology so you can quickly uncover and mitigate cybersecurity issues.
Risk Assessment
Identify risks for each OT asset through the entire asset lifecycle.
Network Device Management
Integrate with monitoring solutions and keep asset information up to date.
Monitoring and Response
Gain peace of mind knowing you have a threat response process in place.
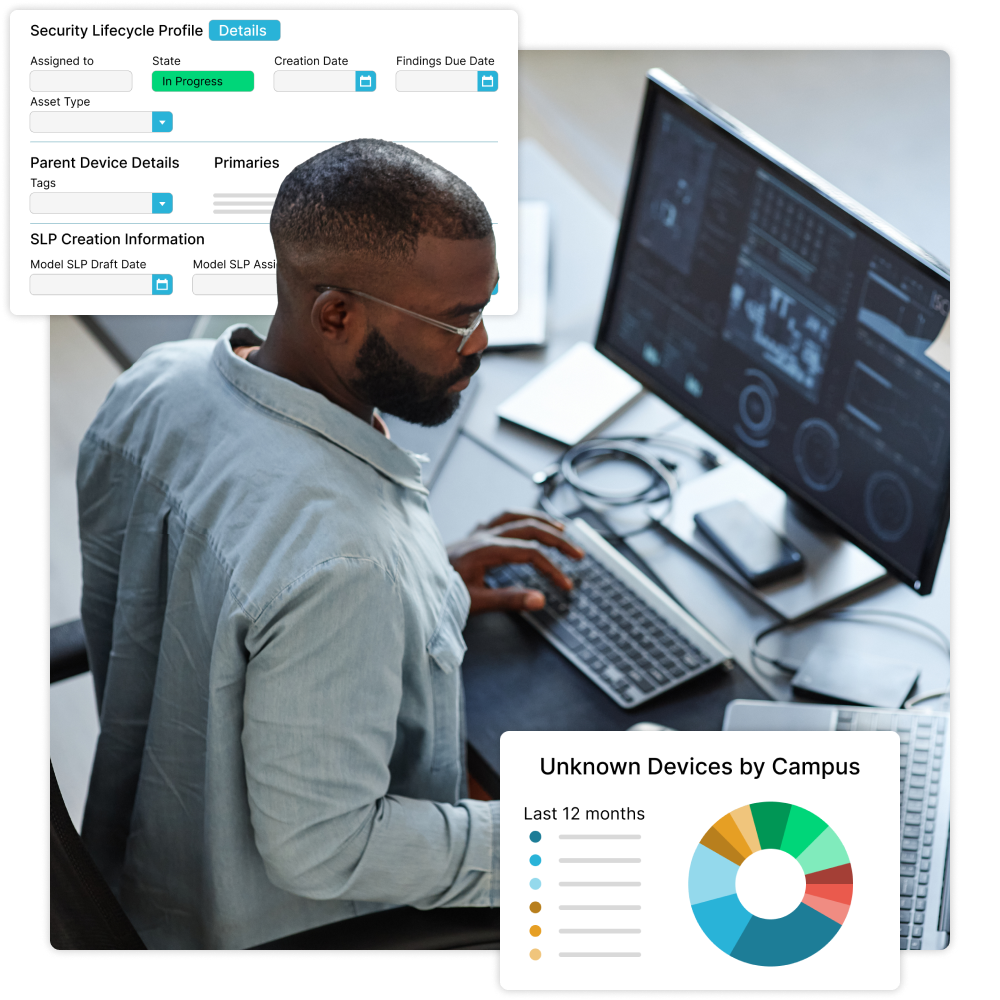
A Triple Threat Against Cyberattacks
Monitor, protect, and mitigate any OT security issues in one place.

Risk Assessment
Have a complete audit trail of all device configuration activities from pre-procurement through device decommissioning.

Network Device Management
Automatically update your device inventory with detailed context from your monitoring tools.

Monitoring and Response
Identify vulnerabilities, prioritize them, and respond with the right resources.
See It In Action
Contact us for a demo to learn how you can start securing your critical OT assets.
REQUEST A DEMO