Understanding the OT Device Security Risk
Operational technology, or OT, is defined as non-IT devices connected to a network. Network connectivity makes your OT devices susceptible to security vulnerabilities allowing hackers to compromise them and disrupt your operations.
This guide provides an overview of the steps necessary to safeguard your OT devices from security threats and vulnerabilities.
OT Device Security Posture
Achieving a strong OT device security posture requires a combination of people, process, and technology. Working together, this helps minimize exposure by ensuring the fastest remediation of security events.
People
Your device support teams need an accurate real-time, trusted inventory of all OT devices, in one location, available wherever they are working, via a mobile device or laptop. Team managers need inventory reports to find out the condition, disposition, and location of OT devices. Security operations center (SOC) personnel need this device inventory to be combined with device monitoring information. This “intelligence hub” empowers them to monitor, control, and manage OT device security.
Process
You need to record device data as part of your standard onboarding process; without it, it’s difficult to determine device disposition, maintenance, and cyber security status. If a cyber threat, vulnerability, or exploit occurs, timely remediation can be difficult or impossible to achieve without a common data model for matching, contextualization, and OT cyber security event correlation.
Technology
Multiple inventory databases and work order management systems make achieving a successful OT device cyber security posture complex, expensive, and time-consuming. There’s a constant need to correlate, contextualize, and normalize data. Consolidating legacy technologies onto a single service management and OT inventory platform is the first step to OT device cyber security.
Nuvolo OT Device Security
Nuvolo OT Security enables this seamless approach of people plus process and technology and accelerates security event remediation. This approach ensures the accessibility and availability of your devices. Nuvolo OT Security helps you achieve the steps needed for a strong cyber security posture, including:
- Single OT device inventory
- Integration with OT device discovery and monitoring tools
- Pre-integrated vulnerability data sources that leverage the National Institute of Standards and Technology (NIST), Common Weakness Enumeration (CWE), Common Platform Enumeration (CPE), and Common Vulnerabilities and Exposures (CVE) vulnerability data imports. And, matching of documented vulnerabilities from NIST/MITRE Corporation
- A rules-based identification algorithm that identifies your OT device or OT devices that are affected by the event or vulnerability. And, the security context and impact of the event, including what patch, configuration change, or mitigating controls are required to then determine the remediation priority
- Orchestration of the next steps, including kicking off remediation workflows to generate a work order or investigative work order
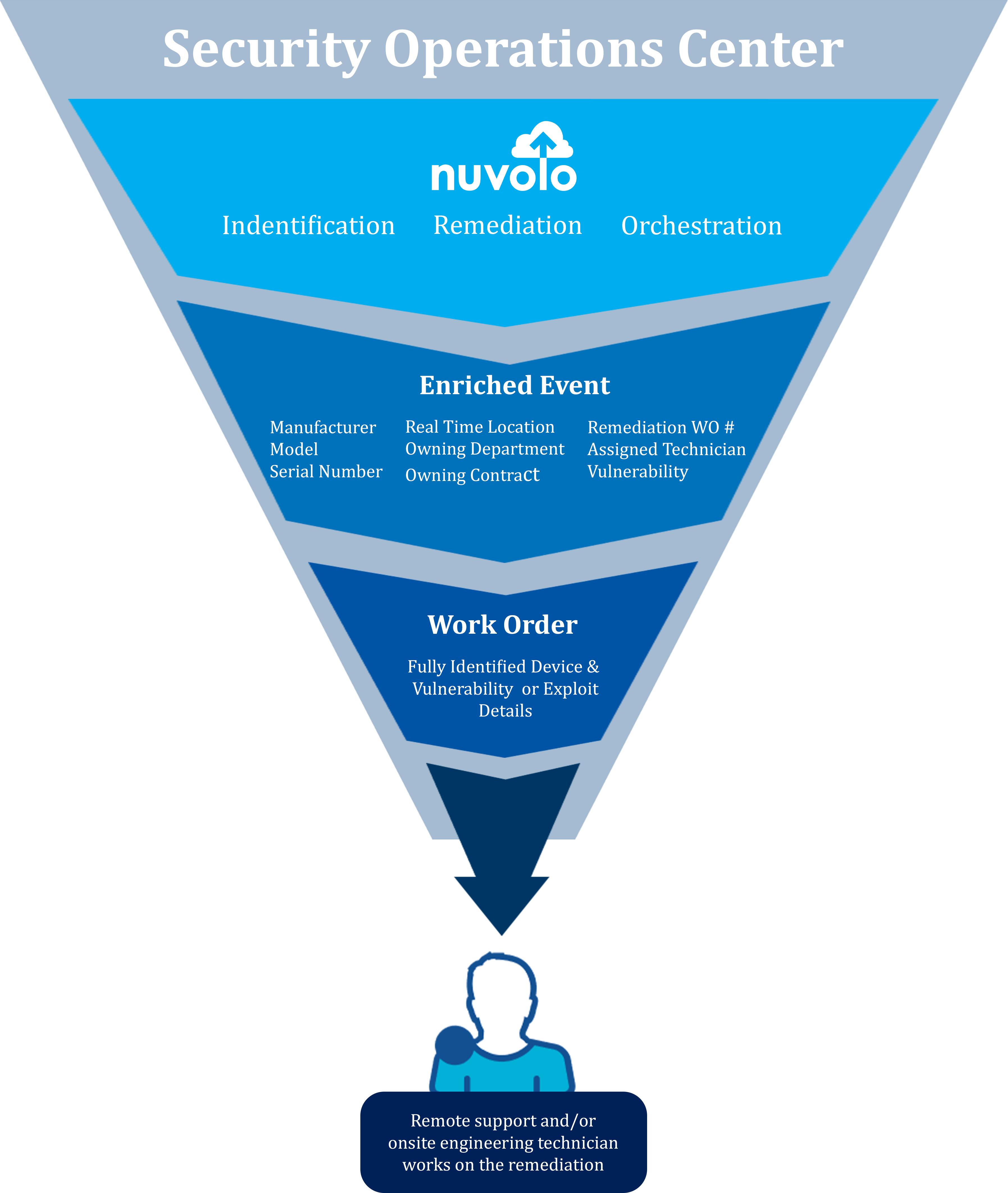
Steps to Operational Technology (OT) Device Security
Step 1: Single OT Device Inventory
A single, trusted inventory system for OT devices helps you manage the entire device lifecycle. Regular, ongoing updates occur when your device support team performs tasks such as routine planned or corrective maintenance, provisioning new devices, or OT device firmware or software updates. The OT inventory system includes data such as:
- Owner
- Device manufacturer
- Device model
- Location
- Department
- Usage
- Serial number
- Latest software version
- Maintenance history
Nuvolo creates a single device inventory based on the ServiceNow PaaS (Platform as a Service) configuration management database (CMDB). This inventory receives data from multiple systems including computerized maintenance management systems (CMMS), and integration with device discovery and monitoring solutions. This integration creates an intelligence hub that is used to correlate events and vulnerabilities against device records from the NIST Cybersecurity Framework 1.1 NVD, CPE, and Mitre CWE.
Nuvolo OT Security manages your non-IT devices, networked, or not, by continually receiving updated discovery, utilization, and security event data. The updates are done with a bi-directional flow of data or an asynchronous flow of data between integration partners’ device discovery and monitoring solutions based on key attributes.
In addition to automated inventory updates, your field technician and OT device engineering teams can manually update the Nuvolo inventory. Providing a holistic approach to device management with the capability to add/remove device records using the Nuvolo mobile app or web application as part of the ongoing device maintenance and onboarding process. This also provides the enrichment of an existing record or creating a totally new record.
Step 2: OT Device Discovery and Monitoring with Supporting Third Party Services
The integration of OT device discovery and monitoring solutions with Nuvolo OT Security enables the discovery, identification, onboarding, assessment, and security remediation for your OT devices within Nuvolo. Integration of Nuvolo with these monitoring systems enables the enrichment of device profiles within the 3rd party systems and provides you with unified IT and OT security event response and risk management visibility.
When the discovered OT device information from a security event is enriched by the inventory data, your data security, IT, and device support teams now all operate with the same data and visibility as part of rapid remediation of security events.
Along with device discovery, Nuvolo OT Security also adds OT device information such as current software versions, location, usage, and context information for each device to be updated during a physical visit by the field technician or device engineer.
Step 3: Pre-Integrated Vulnerability Data Sources
Nuvolo OT Security imports pre-integrated vulnerability data sources. These include the National Institute of Standards and Technology (NIST) Common Weakness Enumeration (CWE), Common Platform Enumeration (CPE), and Common Vulnerabilities and Exposures (CVE) vulnerability data import. And, matching of documented vulnerabilities from NIST/MITRE Corporation across device inventories.
By matching these OT security, utilization, and discovery events against known asset data in the CMMS system like MAC and IP address, serial number, location, owner, Nuvolo OT Security will drive actions of various sorts against your known assets in the system. This device profile gives the rest of the necessary information to remediate a security threat quickly and accurately.
Step 4: Rules-Based Identification Algorithm That Identifies the Device
Nuvolo uses a rules-based identification algorithm that identifies your device or devices affected by the event or vulnerability and matches additional at-risk OT devices within the inventory.
When an OT device security event occurs, the key is that both your information security and device support teams can see the device’s full context. Nuvolo facilitates full knowledge and visibility of the affected devices including usage and operation, device owner, location, and many other attributes as well as the remediation process to be followed. The security context and impact of the event including what patch, configuration change, or mitigating controls are required to then determine the remediation priority.
With this approach, your IT and OT teams can work from a shared view of all affected OT devices. Then a scalable response is possible, including prioritizing those devices that need to be remediated first.
Step 5: Orchestration to Quickly Remediate Security Events
When there are thousands of OT devices in use in your organization, it’s critical to have a scalable, orchestrated, and automated response to security events. The orchestration includes kicking off remediation workflows to generate a work order or investigative work order.
Nuvolo OT Security runs as a scoped app on ServiceNow. What this means is that the OT device inventory, security events, vulnerability assessment and work order response are all tied together in a single, SaaS-based service management platform.
There’s no need to create or buy a new service management platform.
The Nuvolo OT Security solution adds on to the existing NOW platform.
This approach to OT Device Security provides a scalable solution for your OT devices. Nuvolo provides the single trusted data source, integrated with partners’ device discovery, monitoring, and risk assessment to make up an intelligence hub that assists your on-site technicians and remote support teams to make informed remediation decisions.
Nuvolo OT Security provides dynamic workflows and remediation processes to ensure your connected devices are secure and up to date with the latest firmware, software, patches and provides a remediation process for any known vulnerabilities based on NIST Cybersecurity Framework 1.1 NVD, CPE and Mitre CWE.
This orchestration includes tracking and reporting of OT security events through to remediation. This enables OT and IT teams to ensure that security events are resolved to completion