No organization will ever be 100% protected against all security exploits, no matter how much they invest in security. According to NIST, there were over 17,000 common vulnerabilities and exposures (CVEs) reported in 2019. That is an average of 50 new vulnerabilities daily.
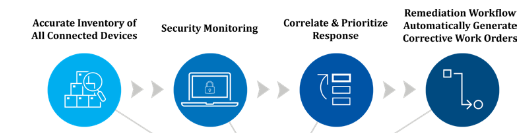
That’s why discovery and having a single inventory of all network-connected devices is crucial. This is because when there’s full context about a device, you can apply an effective response and remediation.
Today, your business may be leveraging a managed security services provider (MSSP) to outsource IT security responsibilities. An MSSP can bring in expert security analysts who leverage best-of-breed tools to assess, monitor and help respond to security events. MSSPs leverage their security operation center (SOC) to provide 24/7 services to reduce the number of IT security personnel you need.
But the story is made more complicated with operational technology (OT) that’s often unmanaged by IT. Depending on what industry you work in, OT can refer to medical devices, lab assets, industrial equipment, or facilities systems such as building automation and control devices.
When OT is connected to your network, the safety, accessibility, and availability of these devices can be disrupted by exploits and security vulnerabilities—and it’s easier than you think. For example, an OT manufacturer may set an unchangeable administrative password on a particular type of device. Hackers are running programs searching the Internet for those devices, and then logging in, taking control, and installing their own malicious software. The devices run normally until the hackers issue instructions, after which they can do anything—from sending meaningless Internet traffic to clog up data connections to even changing device configurations or restarting the device while it’s in use.
OT Is Not IT
Whether you’re using an internal IT team or an outsourced MSSP, both are focused on securing data on traditional IT assets like desktops, laptops, servers, and printers. OT is often unmanaged or worse, unknown, by IT or the MSSP. This means when a security event occurs, there’s a scramble to find out which device is affected, who the device owner is, the location of the device, and how to correct the issue.
An Outsourced Security Model
Let’s assume you’re leveraging an outsourced security model and you’re using an MSSP.
MSSPs have the benefit of mature active monitoring capabilities, vulnerability management tools, and nearly universal remote remediation capabilities for IT devices.
Most of these tools and resources are not available or cannot be used for OT security. Standard operating procedures for OT devices can only be executed by authorized, trained, and certified technicians and engineers. Specialized skills, training, tools, and experience are required for OT device risk mitigation and remediation, and in some cases, OEM or third-party support providers must perform the OT security corrective maintenance activities instead of your MSSP or your internal IT security team.
OT Security with Workflow to Notify Authorized Technicians
An essential part of safeguarding your OT is ensuring 24×7 visibility to help prevent security blind spots. OT discovery should be part of any monitoring of both internal and external activity by OT security professionals with an understanding of medical devices, lab assets, industrial equipment, building automation, and control devices or facilities systems.
The solution is a way for your MSSP to leverage an OT discovery and security monitoring tool that is integrated with a single inventory of all your connected OT. This creates an intelligence hub with an OT inventory system that includes (but is not limited to) data such as:
- Owner
- Device make and model
- Location
- Department
- Usage
- Serial number
- Latest software version
- Maintenance history
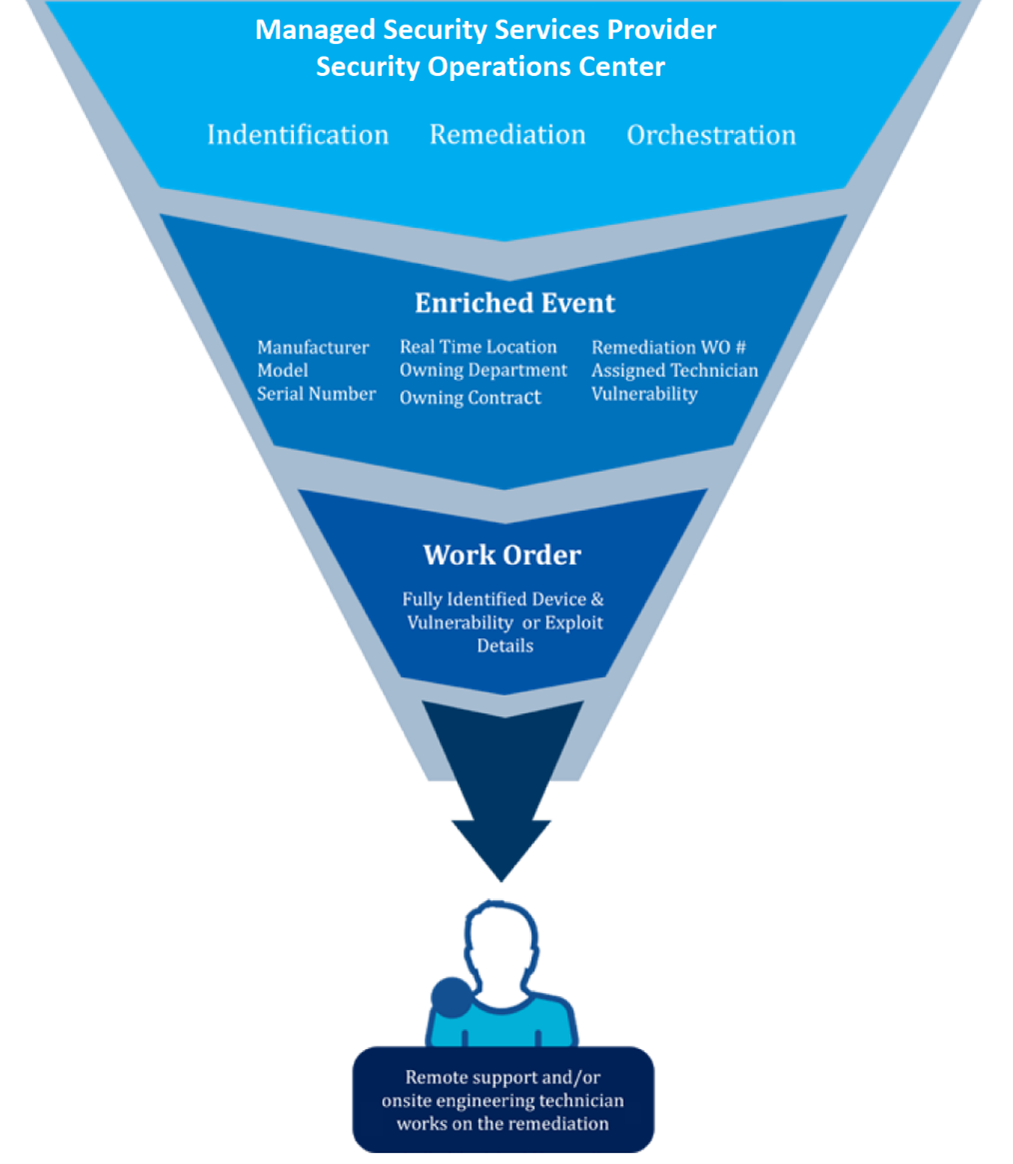
The intelligence hub is used as part of a service management platform for an orchestrated, automated workflow that provides full context of affected devices. This includes owner, location, maintenance history, and any outstanding software or firmware patches. The solution also has the intelligence to correlate across all affected devices.
Most importantly, the MSSP will leverage the solution to initiate the workflow to notify authorized, trained, and certified technicians and engineers to correct all affected devices. The engineer, working remotely, can access the device to deploy software patches, configuration changes, or operating system updates. Alternatively, a field technician can be dispatched by a work order to visit the device and perform the work directly on the equipment. The service management platform will enable the technician to report back to the MSSP on the status of the corrective work.
Nuvolo and MSSPs
Nuvolo OT Security, when integrated with device discovery and security monitoring tools, helps MSSPs offer the ability to ensure the safety, availability, and accessibility of medical devices, lab assets, and facilities systems.
Nuvolo provides a single, trusted data source with a common OT data model. This inventory is kept up to date during the entire device lifecycle—from onboarding through to retirement.
MSSPs can discover and monitor network-connected OT, providing:
- The ability to solve OT security events
- Visibility and persistent OT monitoring
- Identification of new on-network OT
- Master inventory matching and validation
- 360-degree contextual view of OT, including cyber profile, business context, and device history
- Identification, prioritization, and remediation for “like or matching” devices across an organization
- A single, unified view of OT devices and security events for IT and OT teams
- Automated orchestration of multiple stakeholders to resolve OT threats and vulnerabilities
- Tracking and reporting of OT security lifecycle through to remediation
Nuvolo and MSSP for Rapid Remediation of Affected Devices, Assets, and Facilities Systems
Nuvolo provides capabilities to the MSSP’s security operations center (SOC) team that includes access to a single, trusted data source for OT under management. The SOC monitors the OT and then correlates and prioritizes security events. Once completed, remediation activities can take place using trained engineers who are dispatched to perform on-site assessment or remediation. All of this can happen while tracking responses and work order activities in a single platform with robust data and reporting capabilities.
Learn more about Nuvolo OT Security.