This article was originally published in TechNation.
Let’s talk about the elephant in the room: there are many people in healthcare technology management (HTM) that don’t know a lot about protecting medical devices from cyber threats. You may be one of them, and that’s okay. However, that’s no excuse for ignoring the very real cybersecurity risks your hospital and its patients are exposed to every day from your medical devices—aka your operational technology (OT). Ignoring the risks won’t lessen them. The good news is that with the right tools, you don’t have to be a cyber expert to create and manage an effective OT cybersecurity program.
The FDA also has recently been looking into what constitutes an effective medical device cybersecurity program. In June, the agency published a discussion paper on its web site titled “Strengthening Cybersecurity Practices Associated with Servicing of Medical Devices: Challenges and Opportunities.” While the paper was written for discussion purposes only and was not intended to communicate the FDA’s proposed (or final) regulatory expectations regarding the cybersecurity of serviced devices, it does signal the FDA is taking more interest in the topic. The FDA wrote, “Entities that service medical devices are well positioned to help identify cyber exploits and vulnerabilities, and to participate in the continued deployment and maintenance of devices. Cybersecurity is a shared responsibility among stakeholders, including OEMs, healthcare establishments, healthcare providers, and independent service organizations (ISOs).”
It is clear from the points made in the discussion paper that the FDA is seeking to better understand how HTM teams within the hospital (including ISOs) can play a more active role in identifying post-market vulnerabilities and responding efficiently and effectively to them. The paper addresses four key areas:
- Privileged access – developing solutions to mitigate unauthorized access to medical devices without compromising their safe and effective use.
- Identification of cybersecurity vulnerabilities and incidents – and sharing them with the OEM, FDA, Information Sharing and Analysis Organizations, and/or the Department of Homeland Security (DHS).
- Prevention and mitigation of cybersecurity vulnerabilities – through the deployment of OEM-provided and authorized cybersecurity updates and upgrades.
- Product lifecycle challenges and opportunities – related to legacy devices with unsupported operating systems and third-party software.
Even if you’re not an OT cyber expert, anyone with a few years in HTM realizes each of these four areas represents many challenges. For example, how can your HTM organization identify all cybersecurity vulnerabilities and incidents AND prevent and mitigate them? How will you know which of your thousands of networked devices have the latest approved cybersecurity updates/upgrades, and which have unsupported operating systems? If there is a cyber-attack, how will you know what devices are impacted, where they’re located, who supports them, and what needs to be done if all you have are their IP addresses from the IT department? The answer to all these questions is that you can’t without the right tools.
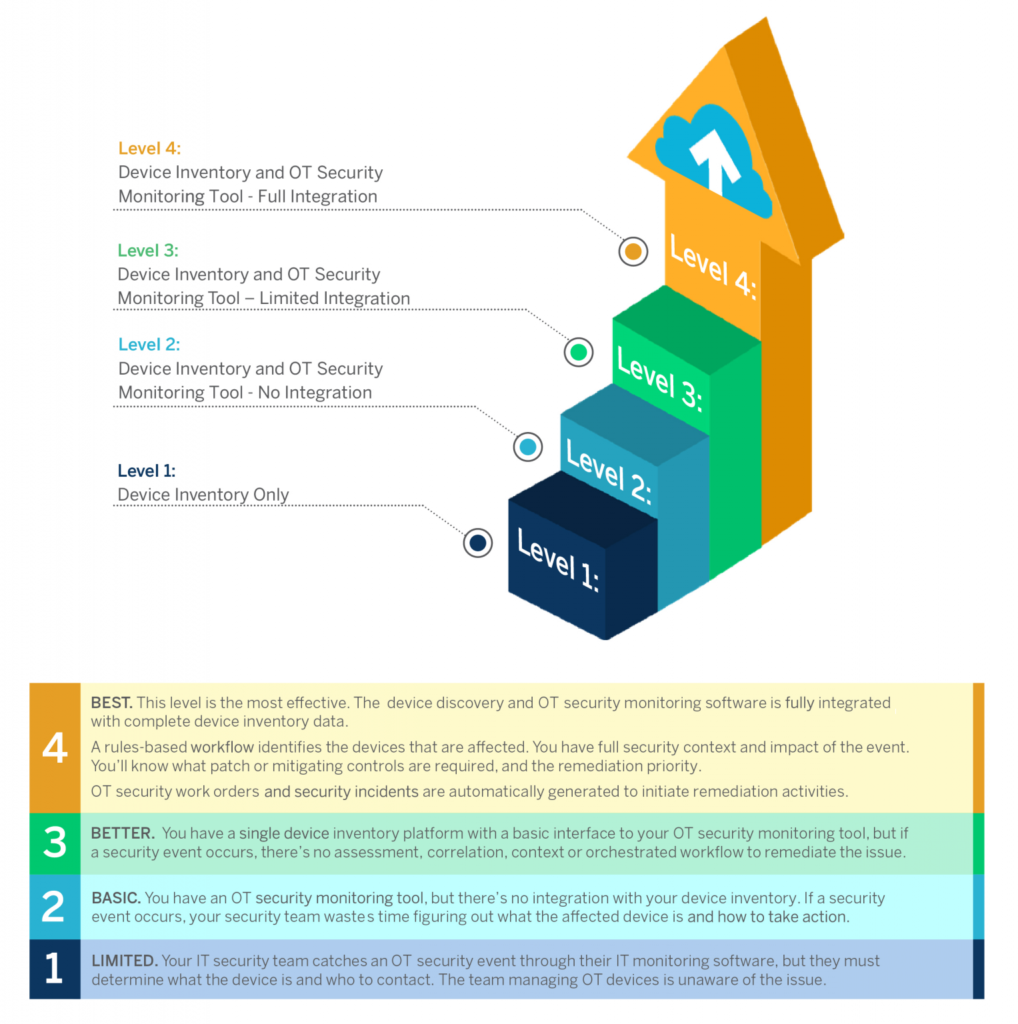
This is why today’s HTM departments must have modern-day computerized maintenance management software (CMMS), such as the Nuvolo Connected Workplace for Healthcare solution. Integrating Nuvolo with an OT network discovery and monitoring tool allows your organization to quickly identify a cybersecurity vulnerability and incident on your networked medical devices. Take that functionality even further and add the Nuvolo OT Security solution to your toolbox, and now you can identify in real-time any new devices added to the network, all their required OT Security-related data that is matched with the asset data in the Nuvolo CMMS (including manufacturer/model, equipment type, location, assigned group/technician, maintenance history, etc.), as well as pre-configured response workflows for fast response to cyber threats.
Adding the following tools to your HTM department’s “toolbox” will allow you to easily create and efficiently manage an effective medical device cybersecurity program:
- Nuvolo Connected Workplace for Healthcare (CMMS)
- Nuvolo OT Security solution
- OT network discovery and monitoring software (Nuvolo integrates with all major vendors)
Learn more by watching the webinar, “Five Lessons Learned to Implement OT Security”. Or read more about the Nuvolo OT Security solution.
About the Author
Heidi Horn, MA, AAMIF is Vice President of Product Marketing-Healthcare for Nuvolo. She has over 20 years of experience as a leader in the healthcare technology management (HTM) industry. Horn was the 2019 recipient of AAMI’s “HTM Leadership Award” and is well-known for her transformational work leading SSM Health’s 120-person HTM department for more than a decade. Horn is also heavily involved with AAMI and serves as a member of AAMI’s Board of Directors as well as chair of AAMI’s Technology Management Council and its HTM Standardization sub-team. She is also an inaugural member of the AAMI Fellow program.